Reading the PciAuditLog table
Implementing the first option for PCI Compliance logs rather than deletes cardholder information. This option allows you to support deferred payment processing (such as for recurring payments, donations, and subscriptions), which is a common reason for wanting to continue to store cardholder data in iMIS. This audit logging populates the PciAuditLog table, which records information to help you account for and track down incidents: who did the accessing, what triggered the logging, what type of event is being logged, and what cardholder information was accessed.
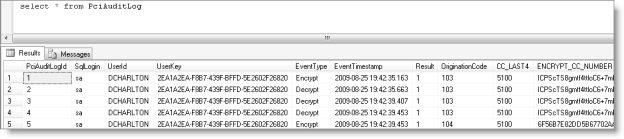
To read the PCI Audit Log
Note: Focus on the UserID for identification (versus the changeable UserKey), and be aware that each transaction can generate multiple unique records in the audit table, all having similar timestamps.
Five types of data events (EventType) trigger iMIS audit logging:
- Decrypt - created by any action that requires an encrypted card number to be decrypted (such as selecting Submitting Deferred Authorizations)
- Encrypt - created by any action that encrypts a card number (such as entering a credit card payment through any interface)
- UpdateLog - any attempt to modify an existing entry in the log
- DeleteLog - any attempt to delete an existing entry in the log
- ChangedEncryptionKey - any time the Reset Encryption Key and Data command is run from DB Maintenance
The origination codes (OriginationCode) identify the source of the action that generated the log entry:
- 100 SQL table itself (originated in the trigger: an attempt to delete or change the log using SQL)
- 101 iMIS Desktop: AsiUtil.dll
- 102 Public/Full view: Asi.dll
- 103 Public/Full view: Secure.dll
- 104 Public/Full view: Asi.iBO.dll
- 105 Change to the encryption key
The Result values tell you about the outcome of the event:
- For Encrypt entries, the result is true if the encryption succeeded (that is, encrypted value exists).
- For UpdateLog and DeleteLog entries, the result is always false because iMIS blocks all updates to and deletions from the log.