Preconfigured security sets
Throughout iMIS, whenever you configure Access Settings, you see a drop-down list of available security settings that you can apply to individual folders and objects. These security sets offer you easier control and faster iMIS performance than defining custom ones.
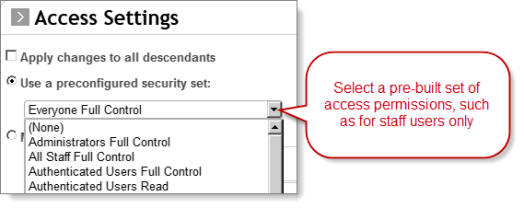
These are the key security sets you should use, from most permissive to least:
- Everyone * — no restrictions, including the public (if they can access this level/context).
- Authenticated Users * — restricts access to users who are signed in (both staff and public members).
- * Staff * — restricts access to users by licensing: Full Staff Full Control limits to Full users, Casual Staff Full Control limits to Casual users, and All Staff Full Control limits to Full and Casual users.
- Administrators * — restricts access to users with the SysAdmin role.
Note: If you do not have the feature named in the security set (such as Certification), do not use the set.
iMIS ships with these pre-built security sets to cut down on the customization you need, for objects that should be neither unsecured (Share) nor locked for you alone (Private). Each security set contains a predefined Access List and permissions (Full Control, Read, Add, Delete, Edit) that are constant for all objects that use it. A Select permission is also available for tagged objects.
When you choose a set, the Current Access List below it updates to show the settings it includes. Look at those details to decide if the selected security set has the permissions you need.
Feature-specific default security
Most feature-specific security sets have three levels (Admin, Manager, User), each of which allows access for any level above it. For example, "Certification Users" grants access for Managers and Admins as well. Note that you can define your own access settings based on User-level security: Roles and Groups.
For example, applying Segmentation Job Default Access security means that
- users in the "SegAdmin" group get control privileges
- users in the "SegMgr" group get Read+Add+Edit+Delete privileges
- users in the "SegUser" group get Read-only privileges
- users in the "SysAdmin" role get control privileges