Implementing Advanced PCI Compliance options and PCI best practices in iMIS is only one small part of your organization's journey. Completing the questionnaire is your first step toward certification: you then arrange for an Authorized Scanning Vendor to test each of your e-commerce IP addresses for security flaws, and after that you apply for certification. It can cost about $100 for scanning of one IP address and help in submitting the questionnaire.
The Payment Card Industry Self Assessment Questionnaire lets your organization determine if you meet mandated security levels for handling credit card transactions. The bulk of the questionnaire deals with firewalls and with clerical and network procedures. It focuses on the effects of software such as Microsoft Windows and SQL Server, as well as network authorizations and security. It does not apply to the vendors of the software you use, but the design of the software can affect what you must do to stay in compliance. Be sure to follow our guidelines for how to implement iMIS for optimal security.
There are a number of versions of the Self-Assessment Questionnaire. Consider the following when determining the correct version of the Self-Assessment Questionnaire to consult:
- SAQ A-EP:
- ASI-hosted and iMIS Advanced Accounting Console used only through an ASI terminal server
- E-commerce only
- No mail orders; no telephone orders
- No face-to-face transactions
- No payment terminals
- SAQ A:
- ASI-hosted and iMIS Advanced Accounting Console only through an ASI terminal server
- Mail orders or telephone orders allowed
- No face-to-face transactions
- SAQ D:
- Self-hosted on own premises
Note: The SAQ C is not applicable to e-commerce channels.
Credit card information is stored using AES encryption which complies with the PCI 3.2 guidelines.
Warning! Changing the PCI Compliance option will reset the GL Interface Type in the iMIS Desktop.
Do the following to configure the PCI compliance options:
- From the Staff site, go to Settings > Finance > General.
- Under PCI Compliance, select one of the following options:
- Do not retain cardholder information - This option prevents iMIS from storing any cardholder data. To use this option, you must disable all CCAuth accounts configured for deferred authorization (or have all related cash accounts removed). If you need to support deferred payment card processing, you must use the Maintain audit log of cardholder information option.
- Maintain audit log of cardholder information - This option causes iMIS to perform audit logging each time a user accesses any cardholder information. Log entries do not exist for access that occurs before the option is enabled or after it is subsequently disabled. This option also logs attempts to access this information by outside processes, such as SQL scripts.
- Decrypt - created by any action that requires an encrypted card number to be decrypted (such as selecting Submitting Deferred Authorizations)
- Encrypt - created by any action that encrypts a card number (such as entering a credit card payment through any interface)
- UpdateLog - any attempt to modify an existing entry in the log
- DeleteLog - any attempt to delete an existing entry in the log
- ChangedEncryptionKey - any time the Reset Encryption Key and Data command is run from DB Maintenance
- 100 SQL table itself (originated in the trigger: an attempt to delete or change the log using SQL)
- 101 iMIS Desktop: AsiUtil.dll
- 102 Public/Full view: Asi.dll
- 103 Public/Full view: Secure.dll
- 104 Public/Full view: Asi.iBO.dll
- 105 Change to the encryption key
- For Encrypt entries, the result is true if the encryption succeeded (that is, encrypted value exists).
- For UpdateLog and DeleteLog entries, the result is always false because iMIS blocks all updates to and deletions from the log.
Warning! If you bypass these options by putting payment card data into user-defined tables, or by using custom encryption methods, you are responsible for PCI Compliance in the handling of that data.
Note: If Do not retain cardholder information is enabled, iMIS saves transactions without cardholder data and shows only gateway reference number and authorization code fields.
Implementing the Maintain audit log of cardholder information option for PCI Compliance logs rather than deletes cardholder information. This option allows you to support deferred payment processing (such as for recurring payments, donations, and subscriptions), which is a common reason for wanting to continue to store cardholder data in iMIS. This audit logging populates the PciAuditLog table, which records information to help you account for and track down incidents: who did the accessing, what triggered the logging, what type of event is being logged, and what cardholder information was accessed.
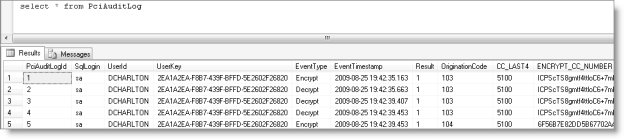
Note: Focus on the UserID for identification (versus the changeable UserKey), and be aware that each transaction can generate multiple unique records in the audit table, all having similar timestamps.
Five types of data events (EventType) trigger iMIS audit logging:
The origination codes (OriginationCode) identify the source of the action that generated the log entry:
The Result values tell you about the outcome of the event:
- Click Save.
- If you chose Do not retain cardholder information, open DB Maintenance (go to Start > ASI > iMIS > Tools > iMIS DB Maintenance Utility) and complete the database preparation steps for your option on the PCI tab. See Database Maintenance for more information.
If the MaxInvalidPasswordAttempts value in the web.config file is modified to a value of 6 or greater, users will be locked out of iMIS. They will see the following message:
The username or password you entered is incorrect.
PCI requires limiting access after six logon attempts. The MaxInvalidPasswordAttempts value in the web.config file must be 5 or fewer in order to meet this requirement.
This requirement is introduced in Service Pack B for PCI compliance.
Depending on which option you choose in AR/Cash Setup, implementing advanced PCI Compliance support requires changes to your iMIS database:
- Remove all existing cardholder information from your iMIS system that predates your new security measures.
- Reset the encryption keys (including removal of previous keys) and re-encrypt cardholder data each year, as required.
DB Maintenance lets you complete these processes easily and reliably.
- Verify that you have a valid backup of your iMIS database before running DB Maintenance commands that modify the database.
- Ensure the database is protected from updates before modifying it, to prevent failures and data problems from changes occurring while entities are being reset/rebuilt/removed:
- Have all users log out.
- Stop webservers from updating the database, such as by stopping the app pool in IIS.
- While users are logged in, you can safely run Analyze Database and Table Details; however, analyzing the database can affect performance.
To maintain PCI compliance with stored cardholder data, you must complete all of the following steps:
- Choose a time when the database can be offline for several hours. Re-encryption can take minutes or hours, depending on your data. Once started, re-encryption must not be stopped.
- In DB Maintenance, open the PCI tab.
- To start the purge, click Reset Encryption Key and Data. A warning prompts you to confirm the process.
- Allow the process to complete without interruption. The output of the process displays in the main window of the utility.
- Click Remove Historical Encryption Keys, or, if postponing that purge, skip to the next step. If you do the purge later, be sure to recycle the application pool then, too.
- Recycle the IIS application pool for each application server that uses this database.
Note: You risk data corruption if you interrupt the process or close DB Maintenance, which appears unresponsive.
Note: Once you remove previous keys, clicking on any encrypted links that have already been embedded in emails (such as create new account emails) will no longer work. The user will see the error "Your session has timed out. Please try your operation again”.
The PCI Data Retention Cleanup task (RiSE > Process Automation) removes outdated credit card information from the database after scanning the database for outdated cardholder information. This is done after a specified period, which is defined in the Staff site at Settings > Finance > General in the Number of days before credit card deletion setting.
The Number of days before credit card deletion setting gives the option to enter a numeric value for the number of days cardholder information should remain in the database. Credit card data will be deleted as defined by this value.
Note: The Number of days before credit card deletion setting supersedes the Purge All Cardholder Information setting in the Advanced Accounting Console.