Last updated on: January 27, 2026
Define how contacts can see and access other contacts through the use of the contact security queries. The contact security queries allow you to define the contacts that are visible by unauthenticated users (guests), authenticated users (contacts with a login), and members.
Contacts returned in these queries can be found when searching your website, and their profile pages can be viewed by website visitors. These contacts may also be found through the API for each respective user type. When viewed through our API and in search, the following information can be obtained for contacts in these queries: Full name, ID, Profile picture, City, State/province, Country, Email, and Phone number.
Important! REST API calls do not use these security queries.
Understanding access levels
Each query grants a specific level of access.
All users access query
All users access query returns group A: All website visitors, authenticated, and unauthenticated users can view group A contacts. If this field is left blank, visitors cannot see the public profiles of any contacts and an error message is displayed.
By default, the following query is used: $/Samples/Security/UserAccess/Contacts available to all users for security. If you wish to modify the default query, you must ensure the results from this query do not return duplicate rows. On the Display tab in the IQA editor, enable the Only display unique results option. This ensures that duplicate contact keys are not returned, as this can cause the query to fail and search indexing to be interrupted, resulting in new contacts not being searchable through the keyword search.
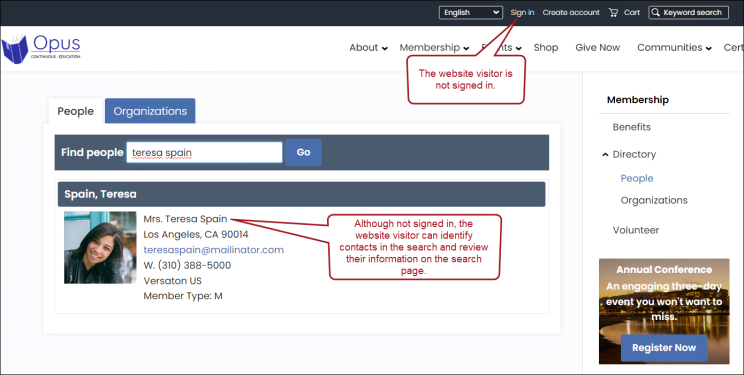
Example: A website visitor who is not logged in uses the website's search to search for Teresa Spain. Since Teresa is included in the All users access query, the website visitor can see her information on the search page. They must login to gain access to her profile.
Authenticated users access query
Authenticated users access query returns group B: Website visitors who are logged in can view groups A and B contacts. Create or edit a query for this field to determine which public profiles all logged-in users can view. Logged-in users will not be able to access public profiles or information for any contacts not included in this query. If this field is left blank, logged-in non-members will effectively have the same level of access as unauthenticated users.
Example: An authenticated user (logged in but not a member) uses the website's search to search for Brian Murphy. Since Brian is included in the Authenticated users access query, the authenticated user can see his information on the search page and can view some information on their profile page.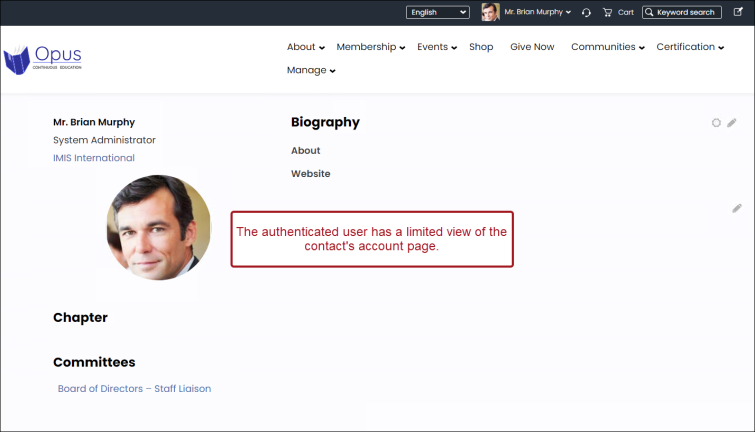
Using the Authenticated users access query for Register Someone Else
If you intend to have events that take advantage of Register Someone Else, do one of the following to ensure authenticated users have access to all contacts available for registration:
- (recommended) Enable Permit public users to register existing contacts. For more information, see Settings: Events.
- (not recommended for security purposes) Include contacts that can be registered in the Authenticated users contact security query. When you include the contacts in the Authenticated users access query, their public profiles are visible to all logged-in users throughout iMIS, including the search results.
Members access query
Members access query returns group C: Members of your organization can view group A, B, and C contacts. Create or edit a query for this field to determine which public profiles members of your organization are allowed to view. If this field is left blank, members will effectively have the same level of access as logged-in non-member users.
Creating access queries
When creating or editing an access query, you must do the following:
- Use the NetContactBasic or NetContactData business object
- Add the iMIS ID property to the Filters tab with In Search? set to Optional
- Add the Contact Key and iMIS ID properties (without an alias) to the Display tab
iMIS provides example queries that you can copy and adjust to fit your organization's needs:
- $/Samples/Security/UserAccess/Contacts available to all users
- $/Samples/Security/UserAccess/Contacts available to members
Visitors to your site might receive an error if they click on the name link of a contact they don’t have permission to view. If your customers report seeing these messages frequently, you might want to review your queries in these fields to loosen the restrictions.
Note: After you select a query to determine your online user access, you can edit it directly from this page by clicking Edit source query.
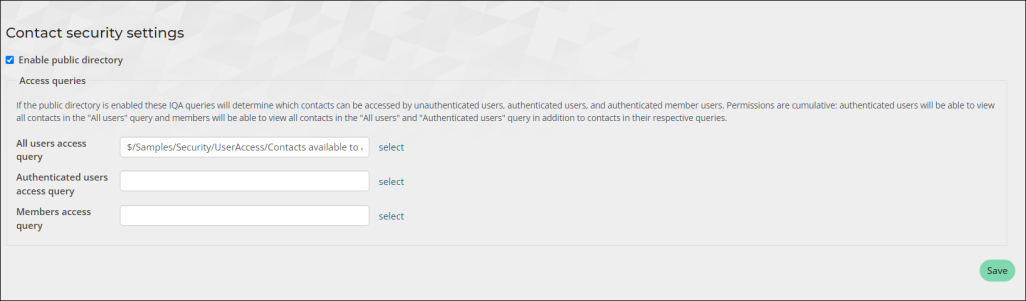
Defining access queries
When the Enable public directory setting is enabled, the Access queries become definable. These queries determine which contacts are accessible by unauthenticated users, authenticated users, and authenticated member users.
Do the following to define the contact security queries:
- Go to Settings > Contacts > Contact security.
- Enable the Enable public directory checkbox.
- Select the query for each access level.
- Click Save.