Last updated on: March 09, 2026
Quick Tutorial Training course
Note: Several of these configuration options allow you to apply Payment Card Industry Data Security Standards (PCI DSS) to your website. PCI DSS applies to companies of any size that accept credit card payments. Please see the PCI Security Standards Council website for more information about PCI compliance.
These configuration options allow system administrators to customize specific security elements for system administrators and those in the Staff group.
Go to Settings > Contacts > Authentication.
In This Article
- Password requirements
Password expiration
Password reuse
Resetting passwords
Forgot password link
Session timeout
Multi-factor authentication (MFA)
Password requirements
By default, passwords must contain at least seven characters with at least one numeric character and at least one alphabetic character. System administrators can change the default password complexity requirements by editing the values at Settings > Contacts > Authentication:
- Minimum characters - The minimum number of characters that must be present in the password. This value must be 7 or greater (minimum length required for PCI compliance).
- Minimum alphabetic characters - The minimum number of alphabetic characters that must be present in the password. This value must be 1 or greater (minimum length required for PCI compliance).
- Minimum numeric characters - The minimum number of numeric characters that must be present in the password. This value must be 1 or greater.
- Minimum capital characters - The minimum number of capital characters that must be present in the password. This value can be any value, including 0.
- Minimum special characters - The minimum number of special characters that must be present in the password. This value can be any value, including 0.
- Maximum invalid password attempts - The maximum number of times a user can attempt to log on with an invalid password before the user is locked out. This value must be between 1 (minimum) and 5 (maximum). This value is 5 by default.
Note: The following are the allowed special characters (spaces are not included in this list): ! " # $ % & ' ( ) * + , - . / : ; < = > ? @ { | } ^
To customize the warning message that appears when someone has failed to meet the minimum password requirements, change the text in the Default message if user password fails minimum password requirement settings field.
Password expiration
When the password expiration option is enabled, passwords for all users (staff and public) will expire after a specified number of days. After the password has expired, users will be prompted to reset their password on their next login. They will be asked for their email address, and then sent a password reset link.
Contact Technical Support if a system administrator is locked out and cannot access their account.
To enable password expiration settings, go to Settings > Contacts > Authentication, then enable the following options:
- Enforce password expiration for staff users - When enabled, all staff users are required to change their password on a regular basis.
- Number of days before password expires - Specify the number of days in which all staff user passwords will expire. The number must be between 1 and 90. If no number is entered, the setting will not enable.
- Enforce password expiration for public users - When enabled, all public users are required to change their password on a regular basis.
- Number of days before password expires - Specify the number of days in which all public users' passwords will expire. The number must be between 1 and 999,999. If no number is entered, the setting will not enable.
When either options are enabled, the Password expires soon alert will notify users of the number of days left before their password expires, based on the value defined for Number of days before password expires.
Password reuse
When users are creating new passwords and try to use a previously used password, they will receive an error message telling them that they must choose a password that is different from a previously used password.
To enable password reuse settings, go to Settings > Contacts > Authentication, then enable the following options:
- Prevent password reuse for staff users – When enabled, all staff users cannot reuse previously used passwords.
- Number of previous passwords that cannot be reused - Specify the number of passwords that must be used before staff users can begin reusing passwords. If no number is entered, the setting will not enable.
- Prevent password reuse for public users - When enabled, all public users cannot reuse previously used passwords.
- Number of previous passwords that cannot be reused - Specify the number of passwords that must be used before users can begin reusing passwords. If no number is entered, the setting will not enable.
Resetting passwords
Review the following information related to resetting passwords.
Public users resetting their own passwords
Although staff users and system administrators have access to reset passwords, it is recommended that staff users direct public users to reset their own passwords.
This can be done in one of the following ways:
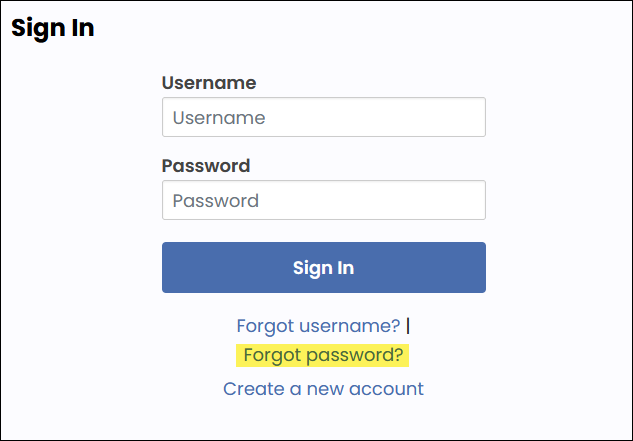
- Direct users to the Forgot password link - Direct the public user to the Sign In page and have them click the Forgot password link.
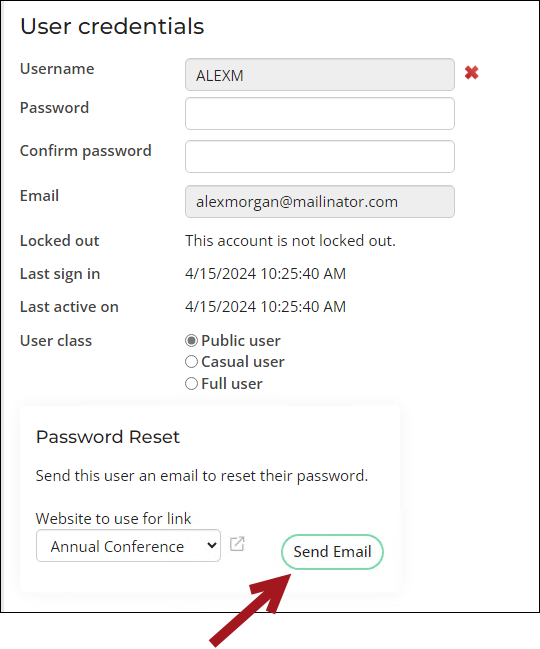
- Send the password reset email - System administrators can send a password reset email directly to a contact from the Security tab of their account page or Community > Security > Users, bypassing the need for the contact to click the forgot password link.
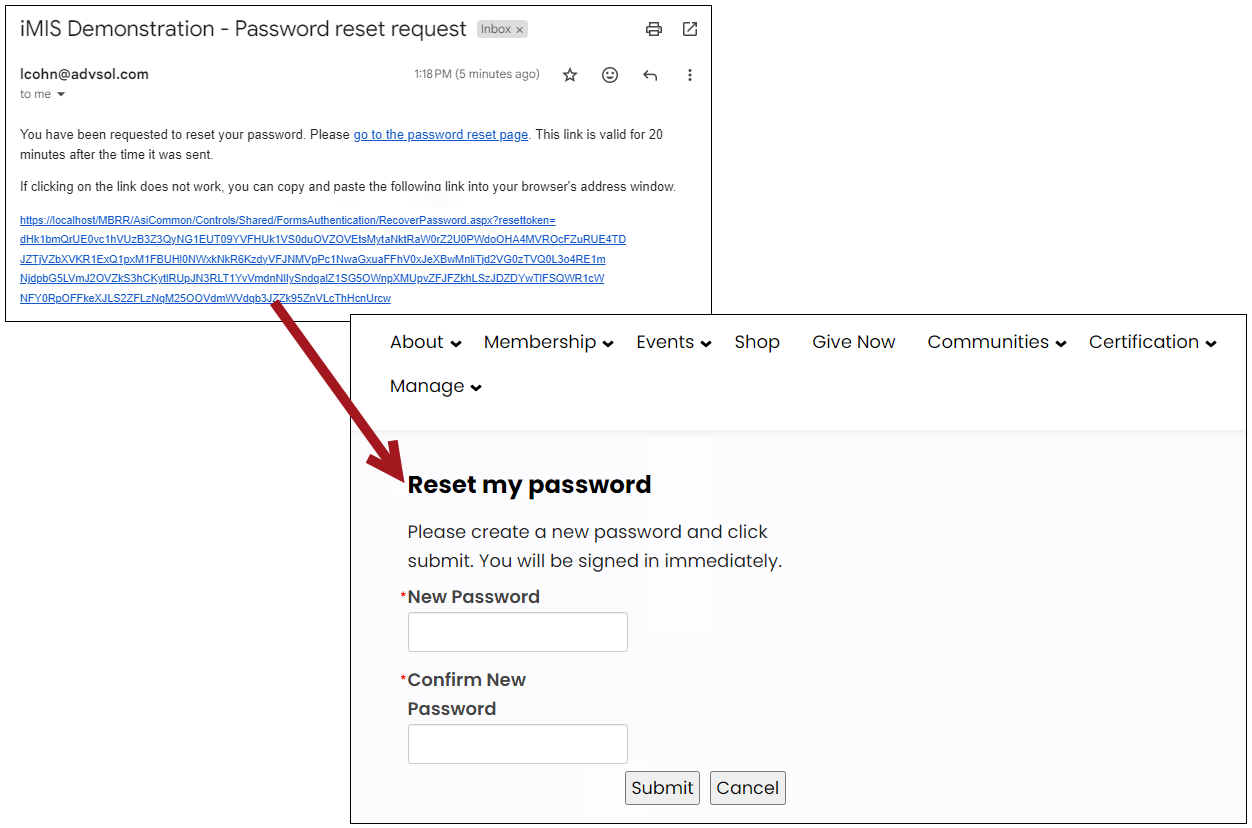
In both cases, users receive the same email with a link to the RecoverPassword shortcut, where they can reset their password securely.
Note: To customize the contents of the password reset email, adjust The body of the email sent to a user when they fill out the "Forgot my password" form (Settings > Contacts > Account management).
DIRECTING Users to the forgot password link
Do the following to direct users to the Forgot password link:
- Verify that the public user's email is current on their iMIS account page.
- Direct the public user to the Sign In page and have them click on the Forgot my password link.
- User resets their own password following the process outlined in the email sent to them.
Sending the password reset email directly to contacts
Staff users can send a password reset email directly to a contact, allowing them to securely update their password without clicking the "Forgot password" link.
Important! At least one active public site with Everyone Full Control access is required to use this feature. If no such site exists, the Password Reset options are not available. For details on configuring site access, see Using Access Settings.
To send the email, do the following:
- Do one of the following:
- Go to the Security tab of the contact’s account page.
- Go to Community > Security > Users and search for the contact.
- Select the public site for the password reset link from the Password Reset area.
- Click Send Email. The contact receives the standard password reset email containing a link to update their password on the selected site securely.
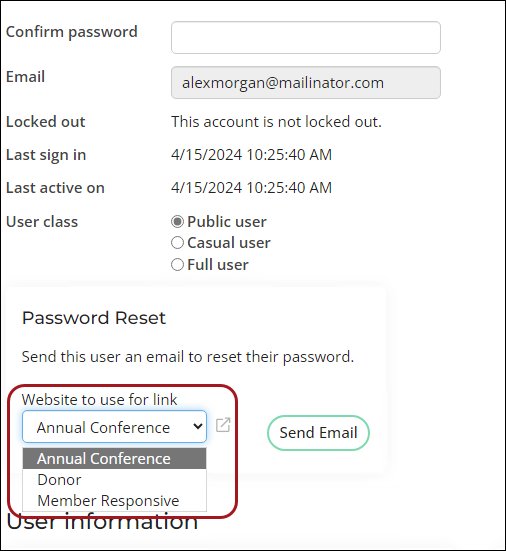
Note: The Website to use for link drop-down only lists active public sites with Everyone Full Control access. To configure site access, see Using Access Settings.
Public users creating their own credentials
If the user has an iMIS account page but does not have existing credentials (e.g., a staff user added them as a contact but did not assign them a username and password) , they can create their own credentials by clicking the Forgot my username link on the Sign In page.
Note: Ensure the Allow "Forgot my username" to automatically create user credentials for existing contacts setting (Settings > Contacts > Account management) is enabled.
Forgot password link
The Forgot password? link is displayed using the Contact Sign In content item. Out-of-the-box, the SignIn shortcut is used to display this content item.
Session timeout
Note: After being enabled, session timeout settings require the user who is enabling the setting to log back in before the setting is activated for that user's session. The session timeout settings apply to system-wide users who log in after either setting is enabled.
When the session timeout warning is displayed, users can choose to Sign Out or Stay Signed In and continue their session. If no selection is made, you will be redirected to the Sign In page to re-enter your iMIS credentials. Please note that any unsaved changes made during that session will be lost.
iMIS recognizes non-idle activities as a browser refresh or saving content. Mouse clicks or moves are not recognized by iMIS as non-idle activities.
To enable session timeout settings, go to Settings > Contacts > Authentication, then enable the following options:
- Enable session timeout for staff users - When enabled, staff users are required to reactivate their session after being idle for a certain amount of time.
- Number of idle minutes before session times out - Specify the number of acceptable idle minutes before a staff users is required to log back in. If no number is entered, the setting will not enable.
- Enable session timeout for public users - When enabled, all public users are required to reactivate their session after being idle for a certain amount of time.
- Number of idle minutes before session times out - Specify the number of acceptable idle minutes before a public user is required to log back in. If no number is entered, the setting will not enable.
Multi-factor authentication (MFA)
iMIS offers multi-factor authentication (MFA).
Before you enable multi-factor authentication
Before you enable multi-factor authentication, there are several items you need to be aware of:
- Multi-factor Authentication is required for staff users.
- All staff and system administrators must have a valid email address:
- If Name.Email and Name_Address.Email are populated, Name.Email is used. If only Name_Address.Email is populated, then Name_Address.Email is used.
- If your staff and system administrators do not specify an appropriate email address, they will be unable to receive an authentication security code and will be unable to log in to iMIS.
- Ensure The default email address for the site (Settings > Organization) is populated with a valid email address.
- Staff users must perform the initial multi-factor setup through the I don’t have a security code link in the Contact Sign In content item.
- Staff users will not be able to sign in to your website using social media accounts or OIDC if multi-factor authentication has been enabled.
- When multi-factor authentication is enabled, iMIS will prompt staff users for a security code every time they log in to iMIS. This also applies to iMIS Quick Start Sites.
- Multi-factor authentication is performed through a public standard for time-based one-time password (TOTP) (IETF RFC 6238). Many authentication tools use this standard, such as:
- Google Authenticator. If you do not have immediate access to Google Authenticator on your phone, you can use a Google Chrome plug-in to access your Google Authenticator through a Chrome browser.
- Microsoft Authenticator
- ZoHo
- 1Password
You must have access to the authenticator on your phone or a similar device.
Enable multi-factor authentication for staff users
Go to Settings > Contacts > Authentication.
The Enable multi-factor authentication for staff users setting is disabled by default. When enabled, staff users (including system administrators) are required to input a security code during login to access all iMIS sites. Delivery of this authentication information requires a valid email address associated with all staff user accounts.
Note: If the Enable multi-factor authentication for staff users setting is enabled, staff users will not be able to use a social media login to access iMIS sites and must use their iMIS credentials to log in to iMIS sites.